Fuzzing: what is it and why bother?
Home -> Fuzzing: what is it and why bother?
Always test your code base for undetected vulnerabilities and bugs
Market demands often place enormous delivery pressures on developers and managers to get code rushed into production. Zealous marketing operations rarely account for the time and effort it takes to build a product that is cyber secure, including third party software.
However, a product that is security compromised in the field can negatively impact availability, reputation, new customer acquisition and share price. The number of security incidents reported every month shows there’s no shortage of malicious actors looking to exploit weak products.
Ensuring that security is built into a product throughout software development life cycles needn’t be like finding your way in the dark. Using proven, highly automated and continuous fuzz testing techniques enables developers to build confidence, and free up valuable time for other items.
1. Improve build quality
Intelligent fuzz testing increases the speed of innovation, whilst giving you and your customers some assurance that new vulnerabilities aren’t inadvertently finding their way into your products.
Fuzz to ensure robust products
Fuzz testing (a.k.a. fuzzing) is a technique used to check the quality and robustness of secure code. Fuzzing is used by many companies secure development life cycles including Microsoft, Google and Cisco. It’s supported by the UK Government’s National Cyber Security Centre (NCSC) and endorsed by US government’s National Institute of Standards and Technology (NIST). Trends in national and international standards, increasingly recommend fuzz testing as an important risk reduction technique.
How fuzz testing works
Fuzz testing is a process that involves sending invalid, unexpected or deliberately malicious test inputs to a target system, often on a massive scale. The purpose is to look for unexpected and undesirable behavior, such as information leaks, process crashes and corrupted data.
Intelligent fuzz testing is a highly effective way to find and prevent security vulnerabilities including the infamous ‘zero-days’ and does not rely on look-up data from libraries. The automated nature of fuzzing can produce tens of thousands of test cases that would be infeasible to generate, execute or analyse manually. Fuzzing therefore commonly discovers software security anomalies that other testing techniques simply fail to identify.
As software and the associated communications interfaces evolve, security flaws tend to creep in. Hackers take advantage of this. Automatic fuzzing can be integrated into secure development life cycles to continuously identify and address the underlying causes of vulnerabilities.
2. Reduce costs of development
Fix issues during production. Remedies typically become much more expensive post deployment.
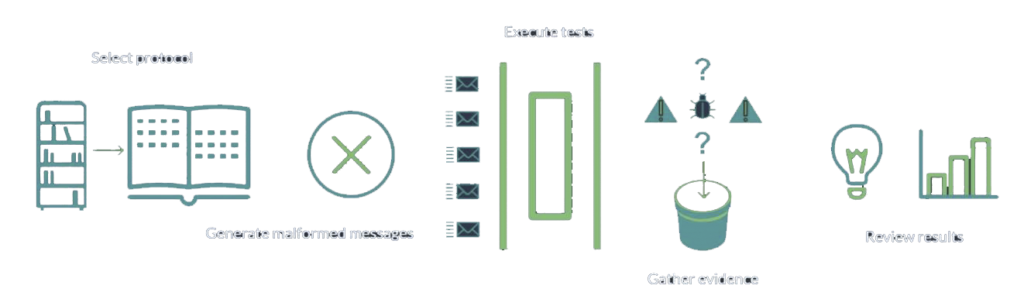
What to look for in a fuzzing solution
Your fuzz testing platform should be able to:
- Create test sets that fit the time you have available and your testing goals
- Tailor the type of coverage to your priorities
- Fuzz any interface, irrespective of whether it uses common or bespoke protocols
- Collect evidence for full traceability and repeatability
- Provide dynamic indicators of interest (things to check out/fix) while the tests are running
- Automatically analyse results and provide meaningful, actionable insights
- Prioritise findings using scoring, to assess risk and make follow up more efficient
Conclusion
When done well, early and regular fuzz testing significantly reduces costly production stage security errors and increases customer confidence in products.
Cost and time savings can be achieved by avoiding retrospective identification of security vulnerabilities and hence the risk of having to replace vulnerable products deployed in the field.
Fuzz testing consistently shows itself to be one of the most useful things you can do to improve the quality of your code base and the overall robustness of your product. It’s one of the most effective techniques you can deploy, relative to the time and cost it takes to undertake.
To understand how fuzzing can work for you, why not talk to us.
3. Reduce risk
Early and regular fuzz testing will vastly reduce the attack surface and help you to prevent unwanted security breaches later.

About
The CyTAL team has decades of fuzz testing experience gained from working across many industry sectors including smart energy and cyber physical systems.
CyTAL’s fuzz testing solution, ProtoCrawler, is widely used by development and quality assurance teams in well-known companies and organisations.

